- Why strncpy is not safe?
- Is the use of strncpy marked as unsafe?
- Why is strncpy insecure?
If you are asking any of the above questions and looking for their answers, well you have come to the right place. Many people ask me to write an article about why strncpy is not safe. In this tutorial, I will explain why strncpy is not safe to use and why it is marked unsafe and insecure.
If you are not familiar with strncpy and you have not used strncpy previously, then it is my recommendation that read my article “how we can create our own custom strncpy function in C”. It gives you a better understanding of the strncpy function.
Following important points that marked strncpy unsafe and insecure:
1. No null terminator:
The strncpy function copies the initial n characters of src to dest and returns the value of dest. If the length of src is longer or equal to the n, a null character is not appended implicitly to the copied destination buffer.
In other words, you can understand that if there is no null character between the first ncharacter of src , the string copied in dest will not be null-terminated.
See the below example,
#include <stdio.h>
#include <string.h>
int main()
{
// The src string length is 12 (including null char).
char src[12] = "Aticleworld";
// The destination array size is 12.
char dest[12];
// copying 5 bytes of src into dest.
//null char will not copy
strncpy(dest, src, 5);
printf("Copied string: %s\n", dest);
return 0;
}
Output:
Copied string: Aticl∟@
Explanation:
You can see printing “Aticl” with some garbage because no trailing null character is available. See the below table for better understanding,
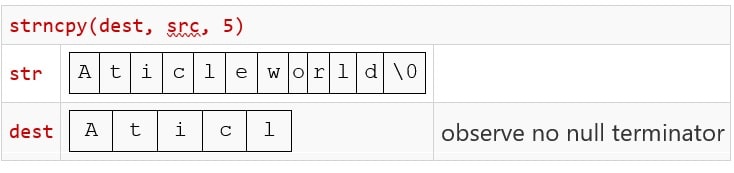
Note: You can solve the problem by adding null characters explicitly.
2. Appending null character till “n”:
If the length of src is smaller to the n, the destination array (dest) is padded with null characters up to the length n.
The following example shows how the strncpy append the null charter till the “n”.
#include <stdio.h>
#include <string.h>
int main()
{
// The src string length is 3 (including null char).
char src[] = "Hi";
// The destination array size is 10.
char dest[10];
// copying 5 bytes of src into dest.
//append null char till 5
strncpy(dest, src, 5);
printf("Copied string: %s\n", dest);
return 0;
}
Output:
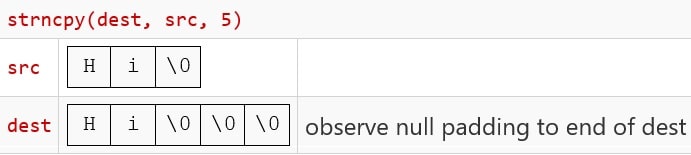
3. Undefined behavior with overlap memory:
The strncpy function shows UB (undefined behavior) if copying takes place between objects that overlap.
4. Overflow:
Personally, I feel that strncpy does not take care of the overflow. If you will try to copy the string beyond the dest array length, this function does not throw any warning. I am not sure about the C standard on this point.
The following example shows how the strncpy function does not care about the boundary of the destination array and copies the string. It leads to undefined behavior.
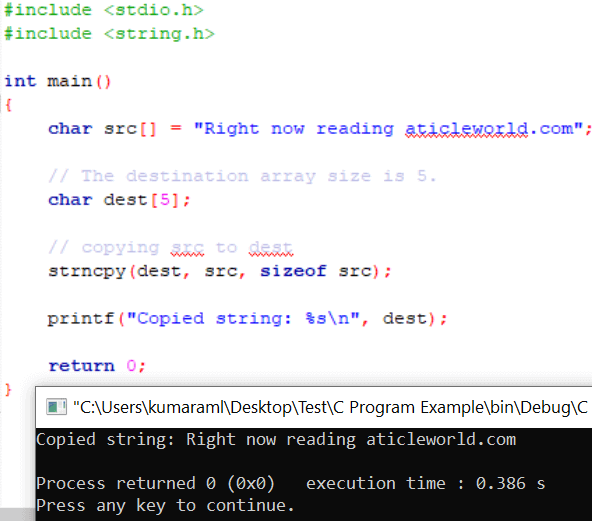
Note: You can use the strncpy_s (since C11) which is safer than strncpy.
Recommended Articles for you:
- C Programming Courses And Tutorials.
- CPP Programming Courses And Tutorials.
- How to make own memmove function in C
- Difference between memmove and memcpy (memmove vs memcpy).
- How to make memcpy function in C.
- Use of strlen function in C.
- strtok function with programming examples.
- strcat function in C with examples code.
- How to use and Implement own strncat in C